Purpose
An analysis that uncovers latent anomalous conditions such as glitches, incompatible functions, false and misleading indications, and requirements non-compliance caused by unintended current paths or improperly integrated hardware / software functions. The System is analyzed to the component level or software instruction assuming no failures are present.
Sneak Analysis (Hardware and/or Software)
Sneak Circuit Analysis
A sneak condition is a latent hardware, software, or integrated condition that may cause an unwanted event to occur or may inhibit a desired event and is not caused by component failure. These conditions are characterized by their random nature and ability to escape detection during the most rigorous of standardized system tests. Sneak conditions can cause improper operation, loss of system availability, program delays, or even death or injury to personnel.
A sneak circuit is an unexpected path or logic flow within a system which, under certain conditions, can initiate an undesired function or inhibit a desired function. The path may consist of hardware, software, operator actions, or combinations of these elements. Sneak circuits are not the result of hardware failure but are latent conditions, inadvertently designed into the system, coded into the software program, or triggered by human error. Four categories of sneak circuits are:
- Sneak Paths - Unexpected paths along which current, energy, or logical sequence flows in an unintended direction.
- Sneak Timing - Events occurring in an unexpected or conflicting sequence.
- Sneak Indications - Ambiguous or false displays of system operating conditions that may cause the system or an operator to take an undesired action.
- Sneak Labels - Incorrect or imprecise labeling of system functions - e.g., system inputs, controls, display buses - that may cause an operator to apply an incorrect stimulus to the system.
Sneak Circuit Analysis
Sneak Circuit Analysis (SCA) was developed in the late 1960's for NASA to verify the integrity and functionality of their designs. Electronic control systems at this time were designed with relays, vacuum tubes, diodes and resistors. They did not contain Integrated Circuits, microprocessors or software like modern systems. Isolating each function from the other functions was a challenge to these early systems because current could inadvertently flow through an unintended path causing false indications, glitches, unintentional outputs, etc. especially when interacting with the equipment throughout it's operational scenarios. Sneak Circuit Analysis was a useful tool to discover all these unintentional circuit paths and assisted in devising solutions to isolate each function. However, as technology advanced, the tools for Sneak Circuit Analysis had to also advance. Sneak Analysis is the term used to describe an increased scope of Sneak Circuit Analysis. In the 1970's, it was recognized that searching current paths did not work
Sneak Analysis
Sneak Analysis includes and far exceeds the coverage of Sneak Circuit Analysis. Sneak Analysis can locate problems in both hardware and software using any technology. The Sneak Analysis tools can integrate several analyses such as Fault Trees, Failure Mode and Effects Analysis (FMEA), Reliability, etc. into a single analysis saving time and project expenses.
Symptoms of sneak conditions include system problems that are non-repetitive through tests or simulations, problems which conventional analyses cannot detect, self-clearing problems, and higher failure rates than expected.
Value
Regardless of the development methodology or design phase, sneak conditions have been uncovered. The benefits of improved safety, reliability, and reduced life cycle costs gained from a properly executed Sneak Analysis have been demonstrated time after time. Sneak Analysis has helped reduce schedule risks and costs by detecting hardware and software errors before test or occurrence of the condition, by recommending corrections to the design, by reducing retest situations, and by reducing maintenance and logistics costs.
The application of Sneak Analysis provides one with increased confidence in the design of the system. The discipline imposed by the Sneak Analysis, with the detailed examination of the design under various conditions, provides additional assurance that the system will function as intended.
Sneak Analysis has a demonstrated record for improving system safety and reliability while reducing overall design and development costs. It has been estimated that for every dollar invested in Sneak Analysis, there are $25 saved in life cycle costs.
Analysis Integration
The incorporation of Sneak Analysis in a development program can complement and facilitate other required analyses. Detailed design review involved in performing a Sneak Analysis can identify misapplications, over stressing, and similar problems. The intermediate by-products of the Sneak Analysis, such as the network trees can materially assist in the performance of other analyses (FMECA, Reliability predictions, RBDs, Fault Trees Analysis, Hazard Analysis, etc), evaluating design changes, and test planning and troubleshooting. Sneak Analysis also complements simulation and testing by uncovering problems that may not be otherwise detected.
When Fault Tree Analysis (FTA) and Sneak Analysis efforts are integrated, the combined contribution of component failures and sneak conditions can be analyzed. A sneak condition by itself may affect only part of a system in a way, which under normal circumstances has no system impact. However, when the sneak condition is combined in the Fault Tree with some combination of failures, the effect of the sneak can be catastrophic.
Methodology
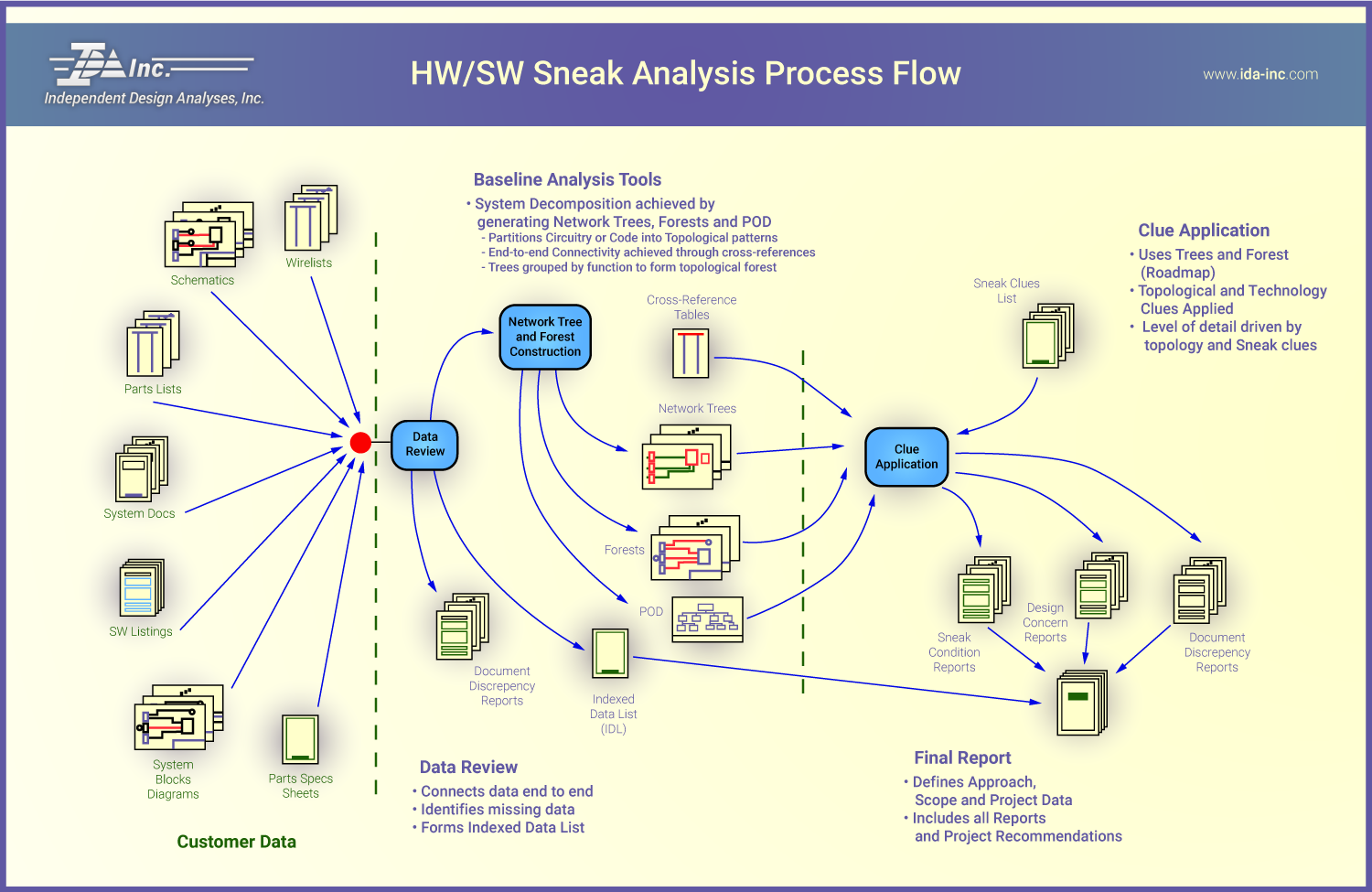
Sneak Analysis is unique from the design process in that it uses different tools (network trees, forests, and clues) to find a specific type of problem. The network trees and forests, which are part of the Baseline Analysis Tools, are topological groupings of the actual system. Each network tree represents a subfunction and shows all inputs that may affect the subfunction output. Forests are constructed by combining the network trees that contribute to a particular system output. A proper forest shows a system output in terms of all of its related inputs. These along with others become the Baseline Analysis Tools.
A typical Sneak Analysis is performed in four phases: (1) data preparation, (2) network tree construction, (3) clue application, and (4) final report preparation, where reporting of Sneak Conditions and Design Concerns occur throughout the first three phases of the analysis.
Analysis Options
Depending on time and cost, a sneak analysis can be focused on only the most critical circuitry or modules, although this runs the risk of a non critical area containing a sneak path into a critical area. The analysis can also be limited to only the interfaces between hardware and software, sub-assembly to sub-assembly, custom design to "off the shelf" design, etc. depending on areas of concern.
Past System Applications
Sneak Analysis has been performed on various types systems in all industries and applications. Listed below are a few actual examples of the types of systems and industries that sneak analysis has been performed:
NASA
- Remote Manipulator Systems
- Star Scanners
- Communication Interface Units
- Manned Maneuvering Unit Isolation Valve Circuitry
- Initiator Firing Test Unit
- Power Distribution
Defense
- Missile Flight Control
- Human Centrifuge Control System
- Digital Engine and Fuel Control
- Drone Flight Control Systems
- Terrain Following Radar
- Vertical Launch Systems
- Inertial Navigation Systems
- Helicopter Emergency Flotation Systems
- Helicopter Stability Augmentation System
Commercial
- Medical Peritoneal Dialysis Cycler Controller
- Wind Turbine System
- Medical Volumetric Infusion Controller (VIC)
- Automobile Electronic System
- Anti-Lock Brake System
- Airbag Diagnostic Module
- Automobile Engine Controller
- Nuclear Reactor Rod Control
- Aircraft Power System
- Helicopter Engine Controller
- Electronics Module Controller
- Four Wheel Drive Controller
